6167 Mobile courses
SALSA LESSON (BEGINNERS) FOR COUPLES & SINGLES IN HAMMERSMITH - CHISWICK EVERY WEDNESDAY @ 7 PM
5.0(62)By Club Azucar - Latin Dance
Salsa lesson for couples & singles in Hammersmith, Chiswick & Barnes with Club Azucar – Latin Dance taught by native instructor Ginu Nunez from Colombia every Monday @ 7 (Beginners) & 8:00 PM (Intermediate & Adv) @ Rivercourt Methodist church, king st, W6 9JT nearest tube station Ravenscourt Park (1-minute walk)

55265 Microsoft© PowerApps
By Nexus Human
Duration 2 Days 12 CPD hours This course is intended for This class has something for everything, from beginners who wish to customise their data entry forms in SharePoint right up to advanced users who need to use advanced formulas to deliver more bespoke actions to their apps. Overview After taking this course, students will be able to: - Understand when to use PowerApp. - Describe the components of PowerApps and their correct use. - Create PowerApps from existing data sources. - Brand PowerApps. - Customize PowerApps beyond just using the automated wizards. - Connect to a range of data sources from Excel to Azure SQL. - Understand the difference between canvas apps and model-driven apps. - Integrate PowerApps with other Office 365 systems ? including Teams and SharePoint Online. - Administer and Maintain PowerApps Students will be taught how to design, test and publish new apps that work with a variety of data sources. We will take users through a selection of well-crafted lessons to help them build new applications for their business. 1 - AN INTRODUCTION TO POWERAPPS * What is PowerApps? * The benefits of apps * How to get PowerApps * Canvas Apps and Model-Driven Apps * License Options and Costs * Discover PowerApps with Templates * Lab 1: Introduction to PowerApps 2 - GETTING STARTED WITH POWERAPPS * Building a new app from a data source * Add, edit and remove controls * Intro to Formulas * Testing an app * App Settings * Publish and Share Apps * Version History and Restore * PowerApps Mobile App * Lab 1: Getting Started 3 - BRANDING AND MEDIA * Less is more * Duplicate Screens * Fonts * Screen Colours and Matching Colours * Screen Backgrounds * Buttons and Icons * Hide on Timer * Size and Alignment by reference * Show and Hide on Timer * Lab 1: Branding and Media 4 - POWERAPPS CONTROLS * Text Controls for Data Entry and Display * Controls ? Drop downs, combo box, date picker, radio button and more * Forms ? Add and edit data in underlying data sources quickly * Charts ? present information in pie, line and bar charts * Lab 1: Build Apps from Blank 5 - DATA SOURCES AND LOGIC * Data Storage and Services * How do I decide which database to use? * Connect to on-premises data - Gateway * What is Delegation? * Specific Data Examples * Displaying Data * Lab 1: Data Source and Logic 6 - MODEL-DRIVEN APPS * What is a model-driven app? * Where will my data be stored? * How do create a model-driven app * Canvas vs model-driven summary * Lab 1: Model-Driven App 7 - POWERAPP INTEGRATION * Embed PowerApps in Teams * Embed PowerApps in SharePoint Online * Start a Flow from a PowerApp * Lab 1: PowerApp Integration 8 - ADMINISTRATION AND MAINTENANCE OF POWERAPPS * Identify which users have been using PowerApps * Reuse an app in another location (move from testing or development to production) * Review app usage * Prevent a user from using PowerApps * Manage environments * Lab 1: Administration and Maintenance ADDITIONAL COURSE DETAILS: Nexus Humans 55265 Microsoft PowerApps training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the 55265 Microsoft PowerApps course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

Creating Videos With Your Phone (Interactive Workshop)
By Clockwork Eye Video Training
Learn to craft top-notch videos for your business using your mobile phone in this interactive workshop. Enhance marketing, visibility, and attract more clients through video. All-in-one workshop for diving into the world of business videos. #VideoCreation #BusinessBoost

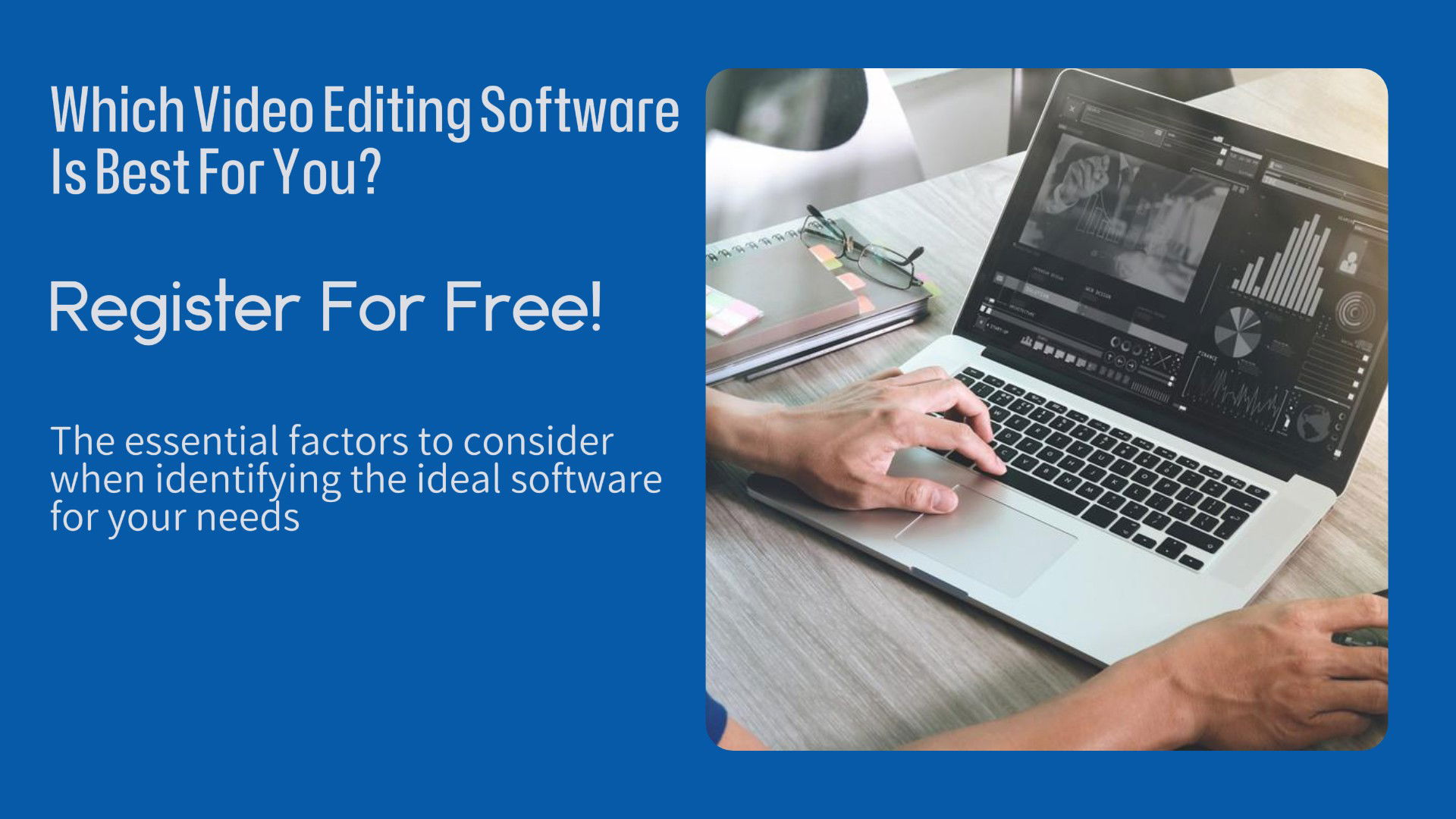
What Video Editing Software is Best For You Webinar - FREE
By Clockwork Eye Video Training
Join our free webinar, "What Video Editing Software is Best For You?", to explore and compare top editing programs, find the best fit for your needs, and enhance your editing skills with expert guidance and live Q&A.
Our 2 day weekend course is a fantastic introduction to sailing, designed to give a taste of sailing or allow you to practice skills in a relaxed environment. It is the perfect setting to find out if sailing is for you, as students are involved in all aspects of sailing the yacht, from basic knot tying to hoisting the sails and steering the boat. You will be taught basic skills and routines on board, whilst enjoying your first exposure to sailing. Price includes accommodation on board one of our yachts, all meals, fuel & mooring fees. Waterproof clothing loan available on request. -------------------------------------------------------------------------------- Our current school boat is the modern 2017 Dufour 382, a fantastic boat to learn and develop your knowledge on; with her spacious deck layout,dual helm and on-deck plotter, she is easy to handle in close and open quarters. We pride ourselves on providing a comfortable, enjoyable sailing experience and guarantee all students their own cabin. Facilities on-board include: • Dual helm • Heating • Fridge • Two toilets each with hot water and showers • Three cabins • Television and radio • Charging points for mobiles • On-deck chart plotter and radar We carry out a deep clean before every course and provide fresh linen and towels. Operating along the picturesque South Devon coast, we venture to prime local cruising locations such as Torbay, Dartmouth, Salcombe and Plymouth. Marinas feature as a daily stop, providing time to reflect and partake in shore-side activities. Our aim is to provide safe fun on the water, allowing you to develop your skills and knowledge in a safe and friendly environment. We use a 3:1 students to instructor raitio, which allows our experienced RYA instructors to tailor courses to the various levels and needs on board, and deliver at a managable pace. Navigation is taught using traditional charting techniques along with electronic methods using E-Series Raymarine chart plotters and Radar. All course prices include accommodation on board, meals for the duration of the course, fuel and mooring fees, and the provision of fresh linen and towels.Waterproofs are available upon request.

What is Reggaeton? It is a blend of Jamaican music with Dancehall & Hip Hop, and the lyrics are mainly in Spanish. Reggaeton became popular in the early 90s within the Latin American you and spread to North America, Europe & Asia. The dancing is very engaging, smooth and versatile. You will experience a real workout, especially in your hips, shoulders and legs toning, it is the real deal!

MD-102T00 Microsoft 365 Endpoint Administrator
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for The Microsoft 365 Endpoint Administrator is responsible for deploying, configuring, securing, managing, and monitoring devices and client applications in a corporate setting. Their duties include managing identity, access, policies, updates, and apps. They work alongside the M365 Enterprise Administrator to develop and execute a device strategy that aligns with the requirements of a modern organization. Microsoft 365 Endpoint Administrators should be well-versed in M365 workloads and possess extensive skills and experience in deploying, configuring, and maintaining Windows 11 and later, as well as non-Windows devices. Their role emphasizes cloud services over on-premises management technologies. In this course, students will learn to plan and execute an endpoint deployment strategy using contemporary deployment techniques and implementing update strategies. The course introduces essential elements of modern management, co-management approaches, and Microsoft Intune integration. It covers app deployment, management of browser-based applications, and key security concepts such as authentication, identities, access, and compliance policies. Technologies like Microsoft Entra ID, Azure Information Protection, and Microsoft Defender for Endpoint are explored to protect devices and data. Prerequisites The Modern Desktop Administrator must be familiar with M365 workloads and must have strong skills and experience of deploying, configuring, and maintaining Windows 11 and later, and non-Windows devices. 1 - EXPLORE THE ENTERPRISE DESKTOP * Examine benefits of modern management * Examine the enterprise desktop life-cycle model * Examine planning and purchasing * Examine desktop deployment * Plan an application deployment * Plan for upgrades and retirement 2 - EXPLORE WINDOWS EDITIONS * Examine Windows client editions and capabilities * Select client edition * Examine hardware requirements 3 - UNDERSTAND MICROSOFT ENTRA ID * Examine Microsoft Entra ID * Compare Microsoft Entra ID and Active Directory Domain Services * Examine Microsoft Entra ID as a directory service for cloud apps * Compare Microsoft Entra ID P1 and P2 plans * Examine Microsoft Entra Domain Services 4 - MANAGE MICROSOFT ENTRA IDENTITIES * Examine RBAC and user roles in Microsoft Entra ID * Create and manage users in Microsoft Entra ID * Create and manage groups in Microsoft Entra ID * Manage Microsoft Entra objects with PowerShell * Synchronize objects from AD DS to Microsoft Entra ID 5 - MANAGE DEVICE AUTHENTICATION * Describe Microsoft Entra join * Examine Microsoft Entra join prerequisites limitations and benefits * Join devices to Microsoft Entra ID * Manage devices joined to Microsoft Entra ID 6 - ENROLL DEVICES USING MICROSOFT CONFIGURATION MANAGER * Deploy the Microsoft Configuration Manager client * Monitor the Microsoft Configuration Manager client * Manage the Microsoft Configuration Manager client 7 - ENROLL DEVICES USING MICROSOFT INTUNE * Manage mobile devices with Intune * Enable mobile device management * Explain considerations for device enrollment * Manage corporate enrollment policy * Enroll Windows devices in Intune * Enroll Android devices in Intune * Enroll iOS devices in Intune * Explore device enrollment manager * Monitor device enrollment * Manage devices remotely 8 - EXECUTE DEVICE PROFILES * Explore Intune device profiles * Create device profiles * Create a custom device profile 9 - OVERSEE DEVICE PROFILES * Monitor device profiles in Intune * Manage device sync in Intune * Manage devices in Intune using scripts 10 - MAINTAIN USER PROFILES * Examine user profile * Explore user profile types * Examine options for minimizing user profile size * Deploy and configure folder redirection * Sync user state with Enterprise State Roaming * Configure Enterprise State Roaming in Azure 11 - EXECUTE MOBILE APPLICATION MANAGEMENT * Examine mobile application management * Examine considerations for mobile application management * Prepare line-of-business apps for app protection policies * Implement mobile application management policies in Intune * Manage mobile application management policies in Intune 12 - DEPLOY AND UPDATE APPLICATIONS * Deploy applications with Intune * Add apps to Intune * Manage Win32 apps with Intune * Deploy applications with Configuration Manager * Deploying applications with Group Policy * Assign and publish software * Explore Microsoft Store for Business * Implement Microsoft Store Apps * Update Microsoft Store Apps with Intune * Assign apps to company employees 13 - ADMINISTER ENDPOINT APPLICATIONS * Manage apps with Intune * Manage Apps on non-enrolled devices * Deploy Microsoft 365 Apps with Intune * Additional Microsoft 365 Apps Deployment Tools * Configure Microsoft Edge Internet Explorer mode * App Inventory Review 14 - PROTECT IDENTITIES IN MICROSOFT ENTRA ID * Explore Windows Hello for Business * Deploy Windows Hello * Manage Windows Hello for Business * Explore Microsoft Entra ID Protection * Manage self-service password reset in Microsoft Entra ID * Implement multi-factor authentication 15 - ENABLE ORGANIZATIONAL ACCESS * Enable access to organization resources * Explore VPN types and configuration * Explore Always On VPN * Deploy Always On VPN 16 - IMPLEMENT DEVICE COMPLIANCE * Protect access to resources using Intune * Explore device compliance policy * Deploy a device compliance policy * Explore conditional access * Create conditional access policies 17 - GENERATE INVENTORY AND COMPLIANCE REPORTS * Report enrolled devices inventory in Intune * Monitor and report device compliance * Build custom Intune inventory reports * Access Intune using Microsoft Graph API 18 - DEPLOY DEVICE DATA PROTECTION * Explore Windows Information Protection * Plan Windows Information Protection * Implement and use Windows Information Protection * Explore Encrypting File System in Windows client * Explore BitLocker 19 - MANAGE MICROSOFT DEFENDER FOR ENDPOINT * Explore Microsoft Defender for Endpoint * Examine key capabilities of Microsoft Defender for Endpoint * Explore Windows Defender Application Control and Device Guard * Explore Microsoft Defender Application Guard * Examine Windows Defender Exploit Guard * Explore Windows Defender System Guard 20 - MANAGE MICROSOFT DEFENDER IN WINDOWS CLIENT * Explore Windows Security Center * Explore Windows Defender Credential Guard * Manage Microsoft Defender Antivirus * Manage Windows Defender Firewall * Explore Windows Defender Firewall with Advanced Security 21 - MANAGE MICROSOFT DEFENDER FOR CLOUD APPS * Explore Microsoft Defender for Cloud Apps * Planning Microsoft Defender for Cloud Apps * Implement Microsoft Defender for Cloud Apps 22 - ASSESS DEPLOYMENT READINESS * Examine deployment guidelines * Explore readiness tools * Assess application compatibility * Explore tools for application compatibility mitigation * Prepare network and directory for deployment * Plan a pilot 23 - DEPLOY USING THE MICROSOFT DEPLOYMENT TOOLKIT * Evaluate traditional deployment methods * Set up the Microsoft Deployment Toolkit for client deployment * Manage and deploy images using the Microsoft Deployment Toolkit 24 - DEPLOY USING MICROSOFT CONFIGURATION MANAGER * Explore client deployment using Configuration Manager * Examine deployment components of Configuration Manager * Manage client deployment using Configuration Manager * Plan in-place upgrades using Configuration Manager 25 - DEPLOY DEVICES USING WINDOWS AUTOPILOT * Use Autopilot for modern deployment * Examine requirements for Windows Autopilot * Prepare device IDs for Autopilot * Implement device registration and out-of-the-box customization * Examine Autopilot scenarios * Troubleshoot Windows Autopilot 26 - IMPLEMENT DYNAMIC DEPLOYMENT METHODS * Examine subscription activation * Deploy using provisioning packages * Use Windows Configuration Designer * Use Microsoft Entra join with automatic MDM enrollment 27 - PLAN A TRANSITION TO MODERN ENDPOINT MANAGEMENT * Explore using co-management to transition to modern endpoint management * Examine prerequisites for co-management * Evaluate modern management considerations * Evaluate upgrades and migrations in modern transitioning * Migrate data when modern transitioning * Migrate workloads when modern transitioning 28 - MANAGE WINDOWS 365 * Explore Windows 365 * Configure Windows 365 * Administer Windows 365 29 - MANAGE AZURE VIRTUAL DESKTOP * Examine Azure Virtual Desktop * Explore Azure Virtual Desktop * Configure Azure Virtual Desktop * Administer Azure Virtual Desktop ADDITIONAL COURSE DETAILS: Nexus Humans MD-102T00 : Microsoft 365 Endpoint Administrator training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the MD-102T00 : Microsoft 365 Endpoint Administrator course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

EC-Council Certified Ethical Hacker (CEH) v12
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for The Certified Ethical Hacking v12 course will significantly benefit security officers, auditors, security professionals, site administrators, and anyone who is concerned about the integrity of the network infrastructure. Overview Information security controls, laws, and standards. Various types of footprinting, footprinting tools, and countermeasures. Network scanning techniques and scanning countermeasures Enumeration techniques and enumeration countermeasures Vulnerability analysis to identify security loopholes in the target organization?s network, communication infrastructure, and end systems. System hacking methodology, steganography, steganalysis attacks, and covering tracks to discover system and network vulnerabilities. Different types of malware (Trojan, Virus, worms, etc.), system auditing for malware attacks, malware analysis, and countermeasures. Packet sniffing techniques to discover network vulnerabilities and countermeasures to defend against sniffing. Social engineering techniques and how to identify theft attacks to audit human-level vulnerabilities and social engineering countermeasures. DoS/DDoS attack techniques and tools to audit a target and DoS/DDoS countermeasures. Session hijacking techniques to discover network-level session management, authentication/authorization, and cryptographic weaknesses and countermeasures. Webserver attacks and a comprehensive attack methodology to audit vulnerabilities in webserver infrastructure, and countermeasures. Web application attacks, comprehensive web application hacking methodology to audit vulnerabilities in web applications, and countermeasures. SQL injection attack techniques, injection detection tools to detect SQL injection attempts, and countermeasures. Wireless encryption, wireless hacking methodology, wireless hacking tools, and Wi-Fi security tools. Mobile platform attack vector, android vulnerability exploitations, and mobile security guidelines and tools. Firewall, IDS and honeypot evasion techniques, evasion tools and techniques to audit a network perimeter for weaknesses, and countermeasures. Cloud computing concepts (Container technology, serverless computing), the working of various threats and attacks, and security techniques and tools. Penetration testing, security audit, vulnerability assessment, and penetration testing roadmap. Threats to IoT and OT platforms and defending IoT and OT devices. Cryptography ciphers, Public Key Infrastructure (PKI), cryptography attacks, and cryptanalysis tools. CEH provides an in-depth understanding of ethical hacking phases, various attack vectors, and preventative countermeasures. It will teach you how hackers think and act maliciously so you will be better positioned to setup your security infrastructure and defend against future attacks. An understanding of system weaknesses and vulnerabilities helps organizations strengthen their system security controls to minimize the risk of an incident. CEH was built to incorporate a hands-on environment and systematic process across each ethical hacking domain and methodology, giving you the opportunity to work towards proving the required knowledge and skills needed to achieve the CEH credential. You will be exposed to an entirely different posture toward the responsibilities and measures required to be secure. Now in its 12th version, CEH continues to evolve with the latest operating systems, tools, tactics, exploits, and technologies. 1 - INTRODUCTION TO ETHICAL HACKING * Information Security Overview * Cyber Kill Chain Concepts * Hacking Concepts * Ethical Hacking Concepts * Information Security Controls * Information Security Laws and Standards 2 - 2 - FOOT-PRINTING AND RECONNAISSANCE * Footprinting Concepts * Footprinting through Search Engines * Footprinting through Web Services * Footprinting through Social Networking Sites * Website Footprinting * Email Footprinting * Who is Footprinting * DNS Footprinting * Network Footprinting * Footprinting through Social Engineering * Footprinting Tools * Footprinting Countermeasures 3 - SCANNING NETWORKS * Network Scanning Concepts * Scanning Tools * Host Discovery * Port and Service Discovery * OS Discovery (Banner Grabbing/OS Fingerprinting) * Scanning Beyond IDS and Firewall * Draw Network Diagrams 4 - ENUMERATION * Enumeration Concepts * NetBIOS Enumeration * SNMP Enumeration * LDAP Enumeration * NTP and NFS Enumeration * SMTP and DNS Enumeration * Other Enumeration Techniques * Enumeration Countermeasures 5 - VULNERABILITY ANALYSIS * Vulnerability Assessment Concepts * Vulnerability Classification and Assessment Types * Vulnerability Assessment Solutions and Tools * Vulnerability Assessment Reports 6 - SYSTEM HACKING * System Hacking Concepts * Gaining Access * Escalating Privileges * Maintaining Access * Clearing Logs 7 - MALWARE THREATS * Malware Concepts * APT Concepts * Trojan Concepts * Virus and Worm Concepts * Fileless Malware Concepts * Malware Analysis * Countermeasures * Anti-Malware Software 8 - SNIFFING * Sniffing Concepts * Sniffing Technique: MAC Attacks * Sniffing Technique: DHCP Attacks * Sniffing Technique: ARP Poisoning * Sniffing Technique: Spoofing Attacks * Sniffing Technique: DNS Poisoning * Sniffing Tools * Countermeasures * Sniffing Detection Techniques 9 - SOCIAL ENGINEERING * Social Engineering Concepts * Social Engineering Techniques * Insider Threats * Impersonation on Social Networking Sites * Identity Theft * Countermeasures 10 - DENIAL-OF-SERVICE * DoS/DDoS Concepts * DoS/DDoS Attack Techniques * BotnetsDDoS Case Study * DoS/DDoS Attack Tools * Countermeasures * DoS/DDoS Protection Tools 11 - SESSION HIJACKING * Session Hijacking Concepts * Application Level Session Hijacking * Network Level Session Hijacking * Session Hijacking Tools * Countermeasures 12 - EVADING IDS, FIREWALLS, AND HONEYPOTS * IDS, IPS, Firewall, and Honeypot Concepts * IDS, IPS, Firewall, and Honeypot Solutions * Evading IDS * Evading Firewalls * IDS/Firewall Evading Tools * Detecting Honeypots * IDS/Firewall Evasion Countermeasures 13 - HACKING WEB SERVERS * Web Server Concepts * Web Server Attacks * Web Server Attack Methodology * Web Server Attack Tools * Countermeasures * Patch Management * Web Server Security Tools 14 - HACKING WEB APPLICATIONS * Web Application Concepts * Web Application Threats * Web Application Hacking Methodology * Web API, Webhooks, and Web Shell * Web Application Security 15 - SQL INJECTION * SQL Injection Concepts * Types of SQL Injection * SQL Injection Methodology * SQL Injection Tools * Evasion Techniques * Countermeasures 16 - HACKING WIRELESS NETWORKS * Wireless Concepts * Wireless Encryption * Wireless Threats * Wireless Hacking Methodology * Wireless Hacking Tools * Bluetooth Hacking * Countermeasures * Wireless Security Tools 17 - HACKING MOBILE PLATFORMS * Mobile Platform Attack Vectors * Hacking Android OS * Hacking iOS * Mobile Device Management * Mobile Security Guidelines and Tools 18 - IOT AND OT HACKING * IoT Hacking * IoT Concepts * IoT Attacks * IoT Hacking Methodology * IoT Hacking Tools * Countermeasures * OT Hacking * OT Concepts * OT Attacks * OT Hacking Methodology * OT Hacking Tools * Countermeasures 19 - CLOUD COMPUTING * Cloud Computing Concepts * Container Technology * Serverless Computing * Cloud Computing Threats * Cloud Hacking * Cloud Security 20 - CRYPTOGRAPHY * Cryptography Concepts * Encryption Algorithms * Cryptography Tools * Public Key Infrastructure (PKI) * Email Encryption * Disk Encryption * Cryptanalysis * Countermeasures ADDITIONAL COURSE DETAILS: Nexus Humans EC-Council Certified Ethical Hacker (CEH) v.12 training program is a workshop that presents an invigorating mix of sessions, lessons, and masterclasses meticulously crafted to propel your learning expedition forward. This immersive bootcamp-style experience boasts interactive lectures, hands-on labs, and collaborative hackathons, all strategically designed to fortify fundamental concepts. Guided by seasoned coaches, each session offers priceless insights and practical skills crucial for honing your expertise. Whether you're stepping into the realm of professional skills or a seasoned professional, this comprehensive course ensures you're equipped with the knowledge and prowess necessary for success. While we feel this is the best course for the EC-Council Certified Ethical Hacker (CEH) v.12 course and one of our Top 10 we encourage you to read the course outline to make sure it is the right content for you. Additionally, private sessions, closed classes or dedicated events are available both live online and at our training centres in Dublin and London, as well as at your offices anywhere in the UK, Ireland or across EMEA.

RYA Competent Crew or Day Skipper - £770 A five day practical course which can accommodate both Day Skipper and Competent Crew candidates, depending on ability and course requirements. We familiarise you with the yacht and spend the week port hopping whilst you gain experience and work towards your qualification. Competent Crew - An ideal way to develop your skills and to start to become an active crew member capable of contributing to the running of a boat. Course content includes learning how to steer the boat, what the sails do, knot-tying, basic seamanship principles and safety procedures. Day Skipper - Putting Day Skipper level theory into practice and taking command of both the boat and crew, you will also learn learn basic engine checks. This includes building on previous experience and developing new skills for close quarter manouevring, handling under power and sail, day navigation, with some night hours. RYA Coastal Skipper / Yachtmaster™ Preparation - £770 A five day practical course for Coastal Skipper or preperation Yachtmaster™ candidates, this course will build and refine your skills and knowledge, including your planning and skippering for passages with pilotage at day and night, boat handling and safety and emergency procedures. If you are looking to gain the Yachtmaster™ Offshore or Coastal Certificate, please let us know and we will arrange an examiner for you. We cannot over emphasise the need for personal preparation for this exam; your theory knowledge should be instinctive and you should exercise safe practices and judgment without being too overcautious. Primarily you will be examined on your ability to be a good skipper. Our emphasis during this course is consolidate all that you have already learned and fine tune any areas that need improvement. You will be expected to be fully skilled in the following areas: communication with crew members, confident and competent boat handling, high standard chart work and navigation, safety briefings and procedures, radio communication, meteorology skills. -------------------------------------------------------------------------------- Our current school boat is the modern 2017 Dufour 382, a fantastic boat to learn and develop your knowledge on; with her spacious deck layout,dual helm and on-deck plotter, she is easy to handle in close and open quarters. We pride ourselves on providing a comfortable, enjoyable sailing experience and guarantee all students their own cabin. Facilities on-board include: • Dual helm • Heating • Fridge • Two toilets each with hot water and showers • Three cabins • Television and radio • Charging points for mobiles • On-deck chart plotter and radar We carry out a deep clean before every course and provide fresh linen and towels. Operating along the picturesque South Devon coast, we venture to prime local cruising locations such as Torbay, Dartmouth, Salcombe and Plymouth. Marinas feature as a daily stop, providing time to reflect and partake in shore-side activities. Our aim is to provide safe fun on the water, allowing you to develop your skills and knowledge in a safe and friendly environment. We use a 3:1 students to instructor raitio, which allows our experienced RYA instructors to tailor courses to the various levels and needs on board, and deliver at a managable pace. Navigation is taught using traditional charting techniques along with electronic methods using E-Series Raymarine chart plotters and Radar. All course prices include accommodation on board, meals for the duration of the course, fuel and mooring fees, and the provision of fresh linen and towels.Waterproofs are available upon request.

CompTIA A+ Part 2
By Nexus Human
Duration 5 Days 30 CPD hours This course is intended for This course is designed for individuals who have basic computer user skills and who are interested in obtaining a job as an entry-level IT technician. This course is also designed for students who are seeking the CompTIA A+ certification and who want to prepare for the CompTIA A+ Core 2 220-1102 Certification Exam. Overview Identify, install and configure Windows Operating System features Perform OS installations and upgrades Identify features and tools of macOS Identify features and tools of Linux OS Summarize security measures and protocols Configure SOHO network security Manage security settings Troubleshoot Windows OS problems Explain change-management best practices Implement workstation backup and recover methods Identify the basics of scripting CompTIA A+ certified professionals are proven problem solvers. They support today?s core technologies from security to cloud to data management and more. CompTIA A+ is the industry standard for launching IT careers into today?s digital world. It is the only industry recognized credential with performance-based items to prove pros can think on their feet to perform critical IT support tasks in the moment. It is trusted by employers around the world to identify the go-to person in end point management and technical support roles. CompTIA A+ is regularly re-invented by IT experts to ensure that it validates core skills and abilities demanded in the workplace. This course follows after the A+ Part 1 course and prepares you for the A+ Core 2 exam 220-1101. Prerequisites While there are no prerequisites for this course, please ensure you have the right level of experience to be successful in this training. LESSON 1: CONFIGURING WINDOWS * Topic 1A: Configure Windows User Settings * Topic 1B: Configure Windows System Settings LESSON 2: MANAGING WINDOWS * Topic 2A: Use Management Consoles * Topic 2B: Use Performance and Troubleshooting Tools * Topic 2C: Use Command-line Tools LESSON 3: IDENTIFYING OS TYPES AND FEATURES * Topic 3A: Explain OS Types * Topic 3B: Compare Windows Editions LESSON 4: SUPPORTING WINDOWS * Topic 4A: Perform OS Installations and Upgrades * Topic 4B: Install and Configure Application * Topic 4C: Troubleshoot Windows OS Problems LESSON 5: MANAGING WINDOWS NETWORKING * Topic 5A: Manage Windows Networking * Topic 5B: Troubleshoot Windows Networking * Topic 5C: Configure Windows Security Settings * Topic 5D: Manage Windows Shares LESSON 6: MANAGING LINUX AND MACOS * Topic 6A: Identify Features of Linux * Topic 6B: Identify Features of macOS LESSON 7: CONFIGURING SOHO NETWORK SECURITY * Topic 7A: Explain Attacks, Threats, and Vulnerabilities * Topic 7B: Compare Wireless Security Protocols * Topic 7C: Configure SOHO Router Security * Topic 7D: Summarize Security Measures LESSON 8: MANAGING SECURITY SETTINGS * Topic 8A: Configure Workstation Security * Topic 8B: Configure Browser Security * Topic 8C: Troubleshoot Workstation Security Issues LESSON 9: SUPPORTING MOBILE SOFTWARE * Topic 9A: Configure Mobile OS Security * Topic 9B: Troubleshoot Mobile OS and App Software * Topic 9C: Troubleshoot Mobile OS and App Security LESSON 10: USING SUPPORT AND SCRIPTING TOOLS * Topic 10A: Use Remote Access Technologies * Topic 10B: Implement Backup and Recovery * Topic 10C: Explain Data Handling Best Practices * Topic 10D: Identify Basics of Scripting LESSON 11: IMPLEMENTING OPERATIONAL PROCEDURES * Topic 11A: Implement Best Practice Documentation * Topic 11B: Use Proper Communication Techniques * Topic 11C: Use Common Safety and Environmental Procedures

Educators matching "Mobile"
Show all 898Search By Location
- Mobile Courses in London
- Mobile Courses in Birmingham
- Mobile Courses in Glasgow
- Mobile Courses in Liverpool
- Mobile Courses in Bristol
- Mobile Courses in Manchester
- Mobile Courses in Sheffield
- Mobile Courses in Leeds
- Mobile Courses in Edinburgh
- Mobile Courses in Leicester
- Mobile Courses in Coventry
- Mobile Courses in Bradford
- Mobile Courses in Cardiff
- Mobile Courses in Belfast
- Mobile Courses in Nottingham







